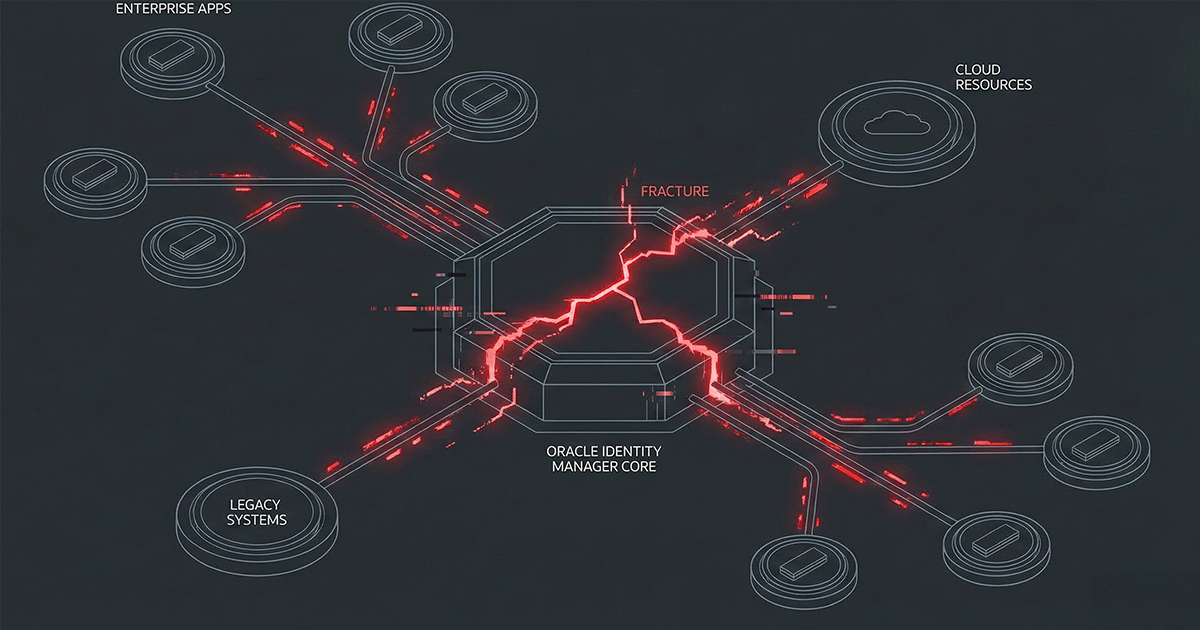
The Identity Fabric: Consolidating the Chaos of 2026
For the past decade, the enterprise security model has been built on a lie: the belief that a "best-of-breed" stack constitutes a defense. The reality of 2026 has exposed this for what it is, a costly architectural failure. Most organizations are currently operating a patchwork of disconnected ...