Beyond MFA: How ShinyHunters Exposed the Authentication Illusion
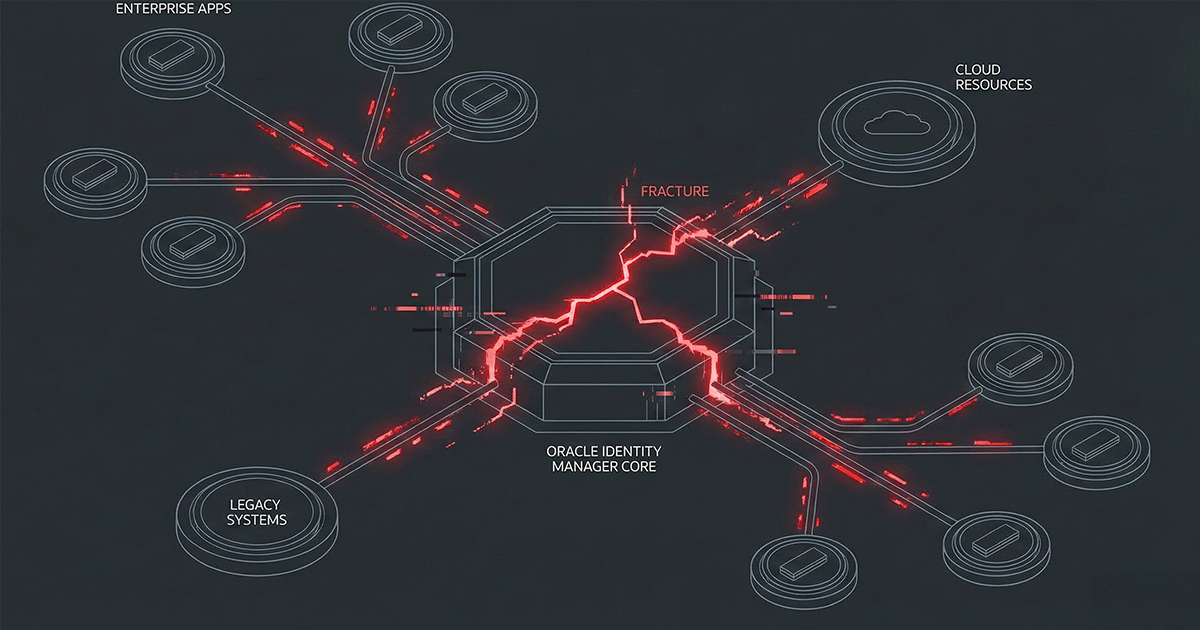
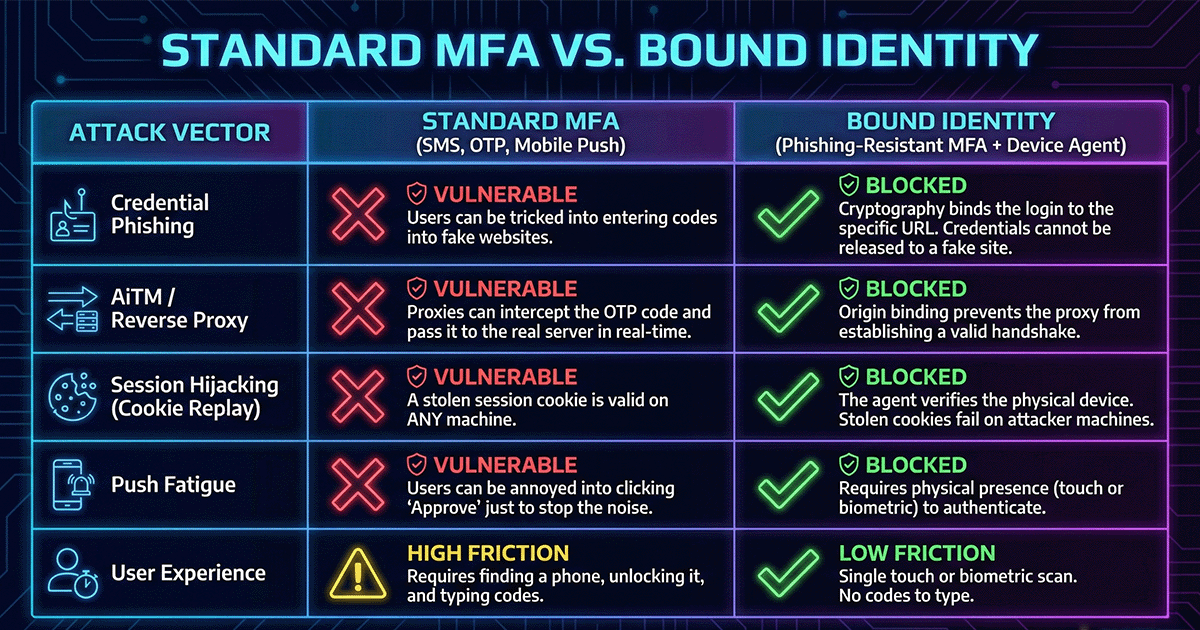
The Mandiant report on ShinyHunters (UNC6661) is not a post-mortem on technical genius; it is an indictment of Static Trust. For years, the industry has treated Multi-Factor Authentication (MFA) as a binary checkbox—a finish line. This is a lethal assumption. Once a user clears the login gate, ...